There is nothing more annoying and frustrating than trying to copy files to a client’s computer using a usb drive and realizing that the clients computer has a virus and it has turned all your files into a shortcut. If you had important files and allow an antivirus to clean the usb drive, you may end up losing the files. This has happened to me on several ocassions and there are times I end up losing files.
It is possible to manually cleanup the USB drive and recover all your files without infecting your computer with the virus. Below are the steps when using a Windows computer.
-
Select the Start button, Control Panel > Appearance and Personalization.
-
Select Folder Options, View tab, make sure:
Show hidden files, folders, and drivesis selectedHide extensions for known file typesis unchecked- Click OK
-
Open windows command prompt
-
Type the following on the command prompt.
attrib -H -R -S /S /D F:\*.*Replace F: with the drive letter assigned to your USB drive
The attrib DOS command is used to change attributes for files. The – sign clears an attribute on a file/folder while a + sets an attribute. -H clears hidden file attribute, -R clears read-only attribute and –S clears the system file attribute. /S processes sub-directories found within the current folder while /D processes folders as well.
After above command, all files/folders on the usb drive are now visible
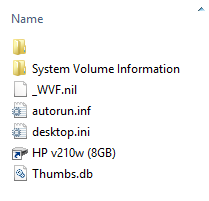
On this ocassion, the virus created a folder with a space and moved all my files and folders to this folder. It also created a shortcut which has the following target
%homedrive%\WINDOWS\System32\rundll32.exe _WVF.nil,rundll32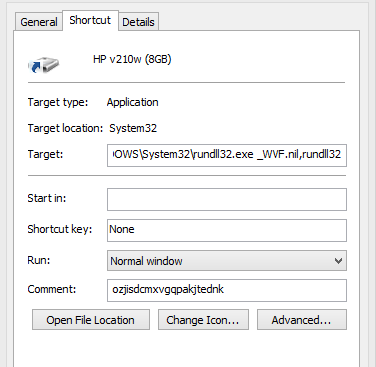
-
I renamed the folder with a space and deleted the shortcut file,
_WVF.nilwhich was being launched through the shortcut and finally let the antivirus cleanup.
In a previous instance, I ran into a similar problem with slight differences. This time, the virus created two folders Z and 000 and 4#UH.ini file in the root of the usb drive. All original files/folders were moved to the Z folder and any Microsoft Word documents converted to executable files. It also placed a csrss.exe in every folder on the usb drive and finally created a shortcut with the following target %homedrive%\WINDOWS\System32\rundll32.exe 4#UH.ini, rundll32
Windows Rundll and Rundll32 Interface have information on rundll32.exe which may give an insight on how the files may be misused and how to identify rogue instances.
